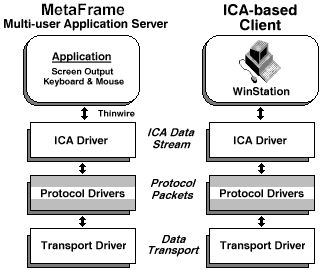
SecureICA Protocol ArchitectureThe Independent Computing Architecture (ICA) is a modular architecture. The encryption layer is negotiated at connect time between the MetaFrame server and MetaFrame client. The ICA Protocol and Transport LayersBeneath the ICA data packets, there are several optional protocol driver layers. Their existence and use is negotiated during the ICA handshaking that occurs at the start of a session. Since these layers sit below ICA, they can be removed or replaced. Additional protocol drivers can also be added. The SecureICA encryption module is inserted at this layer.
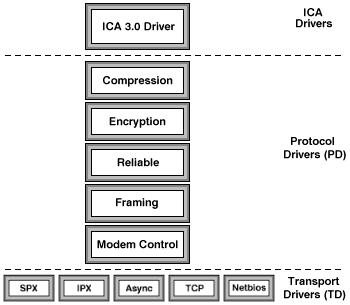
The following diagram shows an expanded view of the ICA protocol layer.
What is encryptedSecureICA encryption is applied to the entire ICA packet. Except for a small encryption header, all of the ICA commands and data are encrypted. This includes:
|
|
 |
Saturday, July 12, 2025 |