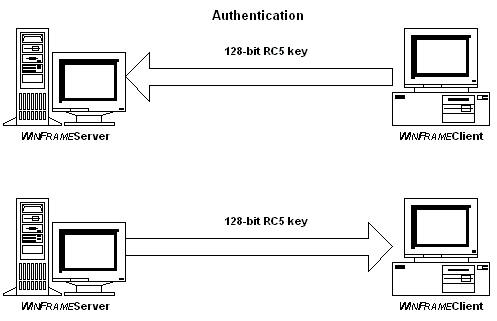
RC5 keys The RC5 algorithm is a symmetric key algorithm. One key is used to both encrypt and decrypt data. The security of the data depends on keeping the key secret. In order to keep data secure, there must be a method of exchanging the RC5 keys without allowing the keys themselves to be copied. The Diffie-Hellman key agreement algorithm generates the same RC5 key on the MetaFrame client and server without exchanging information that compromises the security of the key. The SecureICA Option Pack uses a total of four keys during each session. During user logon, SecureICA uses two 128-bit keys for enhanced security. One key is used to encrypt ICA packets the server sends to the client. The other key is used for client to server communication.
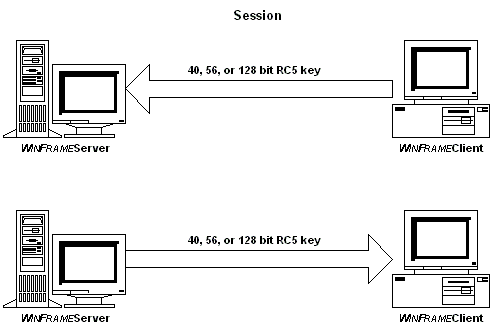
The SecureICA Option Pack uses two 40, 56, or 128 bit keys to encrypt ICA packets after logon. One key is used when the server is sending data to the client. The other key is used for client to server communication. Using two separate keys increases security. The key size to use for the session is specified by the MetaFrame client. An administrator can specify the minimum key size in the WinStation Configuration and User Manager for Domains utilities.
Generating RC5 keysEach time a MetaFrame client connects to a MetaFrame server the four RC5 keys are generated. The Diffie-Hellman algorithm is used when two people need to establish secret keys but they cannot securely transmit those keys to each other. The MetaFrame server and the MetaFrame client establish RC5 session keys using the Diffie-Hellman key agreement algorithm. The MetaFrame server periodically generates two numbers (A and B) using the Encryption Service installed by the SecureICA Option Pack. These numbers are the Diffie-Hellman parameters. The MetaFrame server and client follow the steps outlined below to establish a 1024 bit secret key. This secret key is split into two 128 bit keys used during logon and two 128, 56, or 40 bit keys used after logon.
The MetaFrame client and MetaFrame server both have the same 1024 bit secret key S. The mathematical steps to generate the secret key are described below. Server
Client
S = P1 K2 mod B
Server
S = P2 K1 mod BEven if P2, P1, A and B are known by an intruder, S cannot be derived from that information. The algorithm relies on the mathematical property that (AK1 mod B) K2 mod B = AK1 K2 mod B (AK2 mod B) K1 mod B = AK1 K2 mod B |
|
 |
Monday, March 9, 2026 |